|
|
1.IntroductionLoukhaoukha and Chouinard1 have recently proposed two countermeasures for the problem of false-positive detections2, 3 of watermarks that exists in Abdallah 4 and Aslantas5 singular value decomposition (SVD)-based watermarking schemes without making changes to the original algorithm of those schemes. They claimed that the countermeasures could be applied as an add-on to any SVD-based watermarking schemes that suffered from false-positive detections. The first countermeasure uses a one-way hash function, such as MD5 or SHA-1 during the embedding process to compute digests of the SVD matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\rm W}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\rm W}$\end{document} of the embedded watermark W. The digests or hash values of [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\rm W}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\rm W}$\end{document} (denoted as [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document}) are then kept by the owner so that he can use them in the extraction process if he wants to claim ownership. During the extraction process, the ownership claimant supplies the digests [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document} of his own watermark and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document} are verified with the hash values of the received (and possibly altered by an attacker) matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}${{\widetilde{U}}_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}${{\widetilde{V}}_{\rm W}}$\end{document} (denoted as [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{U}}_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{V}}_{\rm W}}$\end{document}). If [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} ≠ [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{U}}_{\rm W}}$\end{document} or [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document} ≠ [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{V}}_{\rm W}}$\end{document}, then the extraction process halts; otherwise, the extraction process continues. In other words, they claimed that only the rightful owner was able to extract the embedded watermark W if [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{U}}_{\rm W}}$\end{document} ([TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\rm W}$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}${{\widetilde{U}}_{\rm W}}$\end{document}) and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{V}}_{\rm W}}$\end{document} ([TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\rm W}$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}${{\widetilde{V}}_{\rm W}}$\end{document}). The second countermeasure uses an image-encryption (respectively, decryption) method on the watermark W before the embedding process (respectively, after the extraction process). Before the embedding process, watermark W is encrypted to give [TeX:] \documentclass[12pt]{minimal}\begin{document}${W}_{\rm E}$\end{document} and then [TeX:] \documentclass[12pt]{minimal}\begin{document}${W}_{\rm E}$\end{document} is embedded in cover image I to obtain the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}$\end{document}. In the extraction process, [TeX:] \documentclass[12pt]{minimal}\begin{document}$W_E^*$\end{document} is obtained from the possibly corrupted watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_W^*$\end{document} and decrypted to get the watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$W^*$\end{document}, which is perceptually similar to the owner's watermark W. Loukhaoukha and Chouinard1 claimed that a false-positive attack would result in the first extracted image be the attacker's watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}${\widetilde{W}}$\end{document} because the attacker is using the matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}${U_{\widetilde{{\rm W}}}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}${V_{\widetilde{{\rm W}}}}$\end{document}, instead of proper matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\rm W}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\rm W}$\end{document}. However, because the attacker has to feed the first extracted watermark (i.e., [TeX:] \documentclass[12pt]{minimal}\begin{document}${\widetilde{W}}$\end{document} to the decryption process), his final watermark will thus be an encrypted image, which does not help in his ownership claim. In Sec. 2 we show that both countermeasures do not solve the false-positive detection in contrast to what is claimed by Loukhaoukha and Chouinard.1 2.Theorectical Analysis and ExperimentsIn the first countermeasure, the hash values of the watermark W’s SVD matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\rm W}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\rm W}$\end{document} (denoted as [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document}) provided by the ownership claimant does not bind to the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}$\end{document}. Because there is no proof showing that [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document} belong to the rightful owner of the watermark W, therefore an attacker A, who repeats the same hashing process on the SVD matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_A$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_A$\end{document} of his own watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$W_A$\end{document} to obtain [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_A}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_A}$\end{document}, can claim that the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}$\end{document} belongs to him because the extraction process will verify that [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_A}$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{U}}_{\rm W}}$\end{document} ([TeX:] \documentclass[12pt]{minimal}\begin{document}$U_A$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}${{\widetilde{U}}_{\rm W}}$\end{document}) and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_A}$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{V}}_{\rm W}}$\end{document} ([TeX:] \documentclass[12pt]{minimal}\begin{document}$V_A$\end{document} = [TeX:] \documentclass[12pt]{minimal}\begin{document}${{\widetilde{V}}_{\rm W}}$\end{document}). An interesting fact is that since A attacks the scheme, he can provide his own kept [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{U}}_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{{\widetilde{V}}_{\rm W}}$\end{document} which are similar to [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_A}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_A}$\end{document} during the extraction process. The same case applies to the rightful owner, whereby in order to claim the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}$\end{document}, he has to provide his own kept versions of [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{\widetilde{U}_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{\widetilde{V}_{\rm W}}$\end{document} that are similar to [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{U_{\rm W}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$H_{V_{\rm W}}$\end{document} during the extraction process. Therefore, both have equal rights to the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}$\end{document} and no one can prove more than the other. The flaw occurs because the designers1 view the countermeasure in the owner's perspective, ignoring the fact that the attacker can repeat the same steps as the owner. In the second countermeasure, an encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$W_{\rm E}$\end{document} is used in the embedding process. Hence, in the extraction process, after the encrypted watermark is extracted from the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}$\end{document}, it has to be decrypted to obtain the watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$W^*$\end{document}, which is perceptually similar to the original watermark W. The owner needs to keep the SVD’s [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{{\rm W}_{\rm E}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{{\rm W}_{\rm E}}$\end{document} components of the encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$W_{\rm E}$\end{document} so that he can supply the components later in the extraction process. If during the extraction process, an attacker A provides encrypted SVD matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\widetilde{W}_{\rm E}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\widetilde{{\rm W}}_{\rm E}}$\end{document} of his own encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}_{\rm E}$\end{document}, instead of proper matrices [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\widetilde{{\rm W}}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\widetilde{{\rm W}}}$\end{document} as mentioned by the designers,1 then he can still obtain his own encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}_E^*$\end{document}. The encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}_E^*$\end{document} is later decrypted to obtain [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}^*$\end{document}, which is perceptually similar to [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}$\end{document}. This countermeasure fails because the designers1 did not notice that the attacker can simply repeat the same process as the owner in the proof-of-ownership game because they both claim ownership and the extraction process obtains the encrypted SVD matrices from the ownership claimant. Figure 1 shows the cover image I, the owner's watermark W, the owner's encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$W_{\rm E}$\end{document} and the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}$\end{document} after being embedded with [TeX:] \documentclass[12pt]{minimal}\begin{document}$W_{\rm E}$\end{document}. Figure 2 shows the attacker's watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}$\end{document}, the encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}_{\rm E}$\end{document} of the attacker, the extracted encrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}_E^*$\end{document} from the watermarked image [TeX:] \documentclass[12pt]{minimal}\begin{document}$I_{\rm W}^*$\end{document} using [TeX:] \documentclass[12pt]{minimal}\begin{document}$U_{\widetilde{{\rm W}}_{\rm E}}$\end{document} and [TeX:] \documentclass[12pt]{minimal}\begin{document}$V_{\widetilde{{\rm W}}_{\rm E}}$\end{document}, and the final decrypted watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}^*$\end{document}. As can be seen from the experimental results, the final watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}^*$\end{document} that is decrypted from [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}_E^*$\end{document}, is perceptually similar to the attacker's watermark [TeX:] \documentclass[12pt]{minimal}\begin{document}$\widetilde{W}$\end{document} with the correlation coefficient value of 0.948. Fig. 1(a) Cover image, (b) owner's watermark (c) owner's encrypted watermark and (d) watermarked image. 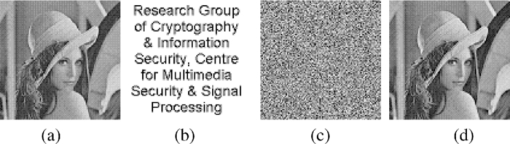 Fig. 2(a) Attacker's watermark, (b) attacker's encrypted watermark, (c) extracted encrypted watermark, and (d) Final decrypted watermark.  A possible countermeasure against false-positive detections would be to avoid6, 7 using the watermark's SVD matrices U and V in the embedding (and thus extraction) process of the Abdallah 4 and Aslantas5 schemes. This removes the influence of SVD matrices U and V on the watermark extraction process, which is the main problem causing false-positive detections. 3.ConclusionsWe have shown that Loukhaoukha and Chouinard1 countermeasures are not able to solve the false-positive detection of the attacker's watermark and thus are not suitable for proof-of-ownership application. This is in contrast to the designers' (Ref. 1) claims that the countermeasures are explicitly designed to solve the problem. The shortfall is because the designers only viewed the countermeasures’ design from the owner's perspective, instead of also from the attacker's perspective as an ownership claimant. When designing the countermeasures as an add-on to the SVD-based watermarking scheme, the designers did not consider that the attacker can follow the same steps as the owner. This leads to the failure of the countermeasures to solve the false-positive detection problem. ReferencesK. Loukhaoukha and J. Chouinard,
“Security of ownership watermarking of digital images based on singular value decomposition,”
J. Electron. Imaging, 19 013007
(2010). https://doi.org/10.1117/1.3327935 Google Scholar
R. Rykaczewski,
“Comments on An SVD-based watermarking scheme for protecting rightful ownership,”
IEEE Trans. Multimedia., 9
(2), 421
–423
(2007). https://doi.org/10.1109/TMM.2006.886297 Google Scholar
X. P. Zhang and K. Li,
“Comments on An SVD-based watermarking scheme for protecting rightful ownership,”
IEEE Trans. Multimedia., 7
(2), 593
–594
(2005). https://doi.org/10.1109/TMM.2005.843357 Google Scholar
E. Abdallah, A. B. Hamza, and P. Bhattacharya,
“Improved image watermarking scheme using fast Hadamard and discrete wavelet transforms,”
J. Electron. Imaging, 16 033020
(2007). https://doi.org/10.1117/1.2764466 Google Scholar
V. Aslantas,
“An optimal robust digital image watermarking based on SVD using differential evolution algorithm,”
Opt. Commun., 282
(5), 769
–777
(2009). https://doi.org/10.1016/j.optcom.2008.11.024 Google Scholar
A. A. Mohammad, A. Alhaj, and S. Shaltaf,
“An improved SVD-based watermarking scheme for protecting rightful ownership,”
Signal Processing, 88 2158
–2180
(2008). https://doi.org/10.1016/j.sigpro.2008.02.015 Google Scholar
H.-C. Ling, R. C.-W. Phan, and S.-H. Heng,
“Analysis on the improved SVD-based watermarking scheme,”
Lect. Notes Comput. Sci., 6059 143
–149
(2010). https://doi.org/10.1007/978-3-642-13577-4 Google Scholar
|

